Lucky
Regular
- Joined
- 14.09.20
- Messages
- 98
- Reaction score
- 433
- Points
- 33
Often the Internet, especially mobile, is in a hurry to "please" us with its unstable work. Whether it is a poor signal level, working from a laptop in motion / by car, or simply the service package has ended. If the internet is cut, the VPN connection is also cut off. At this moment, if you did not have time to take action or reconnect the latter, all programs on your computer will actively begin to access the Internet, but from your real IP address.
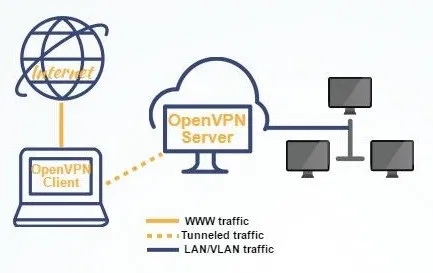
IP flooding may lead to subsequent de-anonymization and determination of your location. In addition, a sudden change of IP address can lead to immediate blocking of the payment system account.
We will use a minimum of tools, mainly system ones, in order to avoid the presence of additional questionable applications in our system. These include obscure closed-source client applications from VPN services, which can potentially contain a large number of vulnerabilities, or even have a built-in function for collecting your personal data, sometimes very critical (gateway IP address, hostname, etc. .)!
Remember, you only need to trust yourself and no one else!
Important! This manual is relevant only for your laptops or PC! Applying this technique to a dedicated server, you personally deprive yourself of access to it! Also, so that nothing interferes with correct operation, it is recommended to remove third-party software with a built-in firewall function.
Let's get started!
Windows 7 / 8.1 / 10 (OpenVPN only) + Bonus! Blocking DNS leaks.
The method consists in correctly configuring the built-in firewall (firewall), where you will need to set the rule "Allow outgoing connections for OpenVPN, deny incoming and outgoing connections for everything else." The method was tested on Windows 7 and 8. Theoretically, it should work on a dozen.
Startup type -> "Automatic" -> Start -> Apply -> Ok. We close the service settings window, we will no longer need it.
1. Click on "Outbound Connection Rules"
2. Create a rule
3. "For the program"
4. "Next"
5. "Program path"
6. Overview
7. Look for and point to the OpenVPN executable file, which is located along the path "C: \ Program Files \ OpenVPN \ bin \ openvpn.exe". The file name is "openvpn.exe"
8. Open
9. Next
10. Allow connection
11. Next
12. We leave everything as it is, then
13. Assign any name for our rule and click "Finish".
Thus, we have created the rule we need. We pass to the next stage.
1. Click on "Windows Firewall with Advanced Security"
2. Properties of Windows Firewall
3. Domain profile -> "Outgoing connections" -> Block
4. Repeat the same for the "Private Profile" tab
5. In the "General profile" tab, on the contrary, allow outgoing connections (by default)
6. Click OK.
For Windows 8-10, other manipulations are required, the manual for which you can find at Сообщество Microsoft.
We open the Network and Sharing Center in any way convenient for you.
2. Be sure to tick the box "Do not ask this question again ..."
3. Change the type to "Enterprise Network" by simply clicking on it with the left mouse button
4. We press close
Done! It's very easy to check - the browser and messengers should not establish a connection until you connect the VPN.
I. Installing ufw
ufw can be found in almost any debian-based repository, so we don't need to include new ones.
We launch the terminal, drive in the command responsible for updating the package cache and directly installing ufw:
Code:
$ sudo apt-get update && sudo apt-get install ufw -y
Code:
$ nslookup "Domain Name"
As an example, it might look like this:
Code:
$ nslookup linux-cryptofree.cryptostorm.net
Server: DNS-SERVER
Address: DNS-SERVER # 53
Non-authoritative answer:
Name: linux-cryptofree.cryptostorm.net
Address: 0.0.0.0
From the domain name “linux-cryptofree.cryptostorm.net” we got the IP address 0.0.0.0, wrote it down or remembered it.
If there are 4 domains in your config, then you need to resolve everything in turn. If the config contains several IP addresses - everything is the same, we write out everything at once.
Occasionally, the opposite situation occurs when there is only one domain name, and the answer contains 2-5-10-20 IP addresses at once. They also need to be written out all! If you are using multiple configs. You get the idea.
Next, let's add the rule itself.
The first line is responsible for blocking all incoming connections. The second is outgoing. The third and fourth allow packets to pass freely through the local VPN adapter interface.
Let's pay attention to the fifth line. It is with this command that we allow outgoing connection to the VPN server. Instead of "0.0.0.0", you need to register the IP address, which we received in 1-3 points. If you got several IP addresses, then the fifth line must be repeated several times, substituting each IP address separately. In the sixth line, we turn on our firewall and add our rule to autoload.
Install the resolvconf package
Code:
$ sudo apt-get update && sudo apt-get install resolvconf -y
This script comes with the latest versions of the OpenVPN package. Check it out, you may not have to create it. If the file is in place, go directly to step 4.
Let's create a file called "update-resolv-conf" in the directory "/ etc / openvpn /"
Code:
$ sudo touch / etc / openvpn / update-resolv-conf
Let's edit it and add the following bash script:
Code:
$ sudo nano / etc / openvpn / update-resolv-conf
After you have pressed Enter, you will see a window for the text editor "nano". Copy the script from here and paste it into the terminal, you can use the right mouse button -> "Paste". In order to save the file, press the hotkey "Ctrl + X", then write the letter "Y" and press Enter. Done, it remains to issue execution rights. We register:
Code:
$ sudo chmod + x / etc / openvpn / update-resolv-conf
We edit the OpenVPN config in any way convenient for you, add 3 lines to the end.
Code:
$ script-security 2
up / etc / openvpn / update-resolv-conf
down / etc / openvpn / update-resolv-conf
We save, reconnect and test (for testing, the site https://dnsleaktest.com/ is suitable.

IP flooding may lead to subsequent de-anonymization and determination of your location. In addition, a sudden change of IP address can lead to immediate blocking of the payment system account.
We will use a minimum of tools, mainly system ones, in order to avoid the presence of additional questionable applications in our system. These include obscure closed-source client applications from VPN services, which can potentially contain a large number of vulnerabilities, or even have a built-in function for collecting your personal data, sometimes very critical (gateway IP address, hostname, etc. .)!
Remember, you only need to trust yourself and no one else!
Important! This manual is relevant only for your laptops or PC! Applying this technique to a dedicated server, you personally deprive yourself of access to it! Also, so that nothing interferes with correct operation, it is recommended to remove third-party software with a built-in firewall function.
Let's get started!

Windows 7 / 8.1 / 10 (OpenVPN only) + Bonus! Blocking DNS leaks.
The method consists in correctly configuring the built-in firewall (firewall), where you will need to set the rule "Allow outgoing connections for OpenVPN, deny incoming and outgoing connections for everything else." The method was tested on Windows 7 and 8. Theoretically, it should work on a dozen.
I. We turn on the Windows Firewall service.
In order to implement your plan, you first need to make sure that the Windows Firewall service is running on your computer. To do this, go to the "Windows Service Manager" in any way convenient for you.- Method 1: Start -> Run -> Enter the line "services.msc" (without quotes) -> Press Enter.
- Method 2: Start -> Control Panel -> Category "small icons" -> "Administrative Tools" -> "Services"
- Method 3: your own way
Startup type -> "Automatic" -> Start -> Apply -> Ok. We close the service settings window, we will no longer need it.
II. We create rules for the firewall.
Open the firewall settings in any way convenient for you.- Method 1: Start -> Run -> Enter the line "wf.msc" (without quotes) -> Press Enter
- Method 2: Start -> Control Panel -> Category "small icons" -> "Windows Firewall" -> menu on the left "Advanced options"
- Method 3: your own way
1. Click on "Outbound Connection Rules"
2. Create a rule
3. "For the program"
4. "Next"
5. "Program path"
6. Overview
7. Look for and point to the OpenVPN executable file, which is located along the path "C: \ Program Files \ OpenVPN \ bin \ openvpn.exe". The file name is "openvpn.exe"
8. Open
9. Next
10. Allow connection
11. Next
12. We leave everything as it is, then
13. Assign any name for our rule and click "Finish".
Thus, we have created the rule we need. We pass to the next stage.
III. We prohibit outgoing connections on all types of networks, except the public one.
1. Click on "Windows Firewall with Advanced Security"
2. Properties of Windows Firewall
3. Domain profile -> "Outgoing connections" -> Block
4. Repeat the same for the "Private Profile" tab
5. In the "General profile" tab, on the contrary, allow outgoing connections (by default)
6. Click OK.
IV. Change the type of the current connection to "Public".
It remains for us to change the type of the current connection to "public". This must be done for each new network, otherwise our rule will simply not work and let traffic leak if the VPN is disconnected! Yes, it's Windows, baby (uninstall ASAP and install Linux). Let's describe how to do this on Windows 7.For Windows 8-10, other manipulations are required, the manual for which you can find at Сообщество Microsoft.
We open the Network and Sharing Center in any way convenient for you.
- Method 1: Start -> Run -> Enter the line "control.exe / name Microsoft.NetworkandSharingCenter" (without quotes) -> Press Enter.
- Method 2: Start -> Control Panel -> Category "small icons" -> "Network and Sharing Center"
- Method 3: your own way
2. Be sure to tick the box "Do not ask this question again ..."
3. Change the type to "Enterprise Network" by simply clicking on it with the left mouse button
4. We press close
V. Warning! IMPORTANT!
- If a pop-up window of the firewall suddenly appears, it is also a request to "allow this program to access the network?" Otherwise, the application will "leak".
- Never allow other programs to automatically add firewall rules! They can damage the installation!
VI. A universal way to block DNS leaks.
Starting with version 2.3.9, the OpenVPN developers have implemented a built-in function to block local DNS servers. To use it, you just need to edit the configuration file by opening it with notepad and add the line "block-outside-dns" (without quotes) to the end of the config file, then save, reconnect and test. You can do this on this website DNS leak testDone! It's very easy to check - the browser and messengers should not establish a connection until you connect the VPN.
Disconnecting the Internet when VPN is disconnected (Linux). Blocking DNS leaks.
The method consists in installing and configuring the simplest firewall for beginners - ufw (UncomplicatedFirewall) on Debian-like distributions. No obscure iptables chains and other jungles.I. Installing ufw
ufw can be found in almost any debian-based repository, so we don't need to include new ones.
We launch the terminal, drive in the command responsible for updating the package cache and directly installing ufw:
Code:
$ sudo apt-get update && sudo apt-get install ufw -y
II. Add and apply rules.
First, we need to find out the IP address of the VPN server in order to add it to the chain of rules for outgoing connections.- Open the config with any notepad
- The VPN server IP address is located opposite the "remote" line. If you have a domain name instead of an IP address, then you need to convert it and replace it in the config. To do this, run the command in the terminal:
Code:
$ nslookup "Domain Name"
As an example, it might look like this:
Code:
$ nslookup linux-cryptofree.cryptostorm.net
Server: DNS-SERVER
Address: DNS-SERVER # 53
Non-authoritative answer:
Name: linux-cryptofree.cryptostorm.net
Address: 0.0.0.0
From the domain name “linux-cryptofree.cryptostorm.net” we got the IP address 0.0.0.0, wrote it down or remembered it.
If there are 4 domains in your config, then you need to resolve everything in turn. If the config contains several IP addresses - everything is the same, we write out everything at once.
Occasionally, the opposite situation occurs when there is only one domain name, and the answer contains 2-5-10-20 IP addresses at once. They also need to be written out all! If you are using multiple configs. You get the idea.
Next, let's add the rule itself.
The first line is responsible for blocking all incoming connections. The second is outgoing. The third and fourth allow packets to pass freely through the local VPN adapter interface.
Let's pay attention to the fifth line. It is with this command that we allow outgoing connection to the VPN server. Instead of "0.0.0.0", you need to register the IP address, which we received in 1-3 points. If you got several IP addresses, then the fifth line must be repeated several times, substituting each IP address separately. In the sixth line, we turn on our firewall and add our rule to autoload.
III. Blocking DNS leaks.
Install the resolvconf package
Code:
$ sudo apt-get update && sudo apt-get install resolvconf -y
This script comes with the latest versions of the OpenVPN package. Check it out, you may not have to create it. If the file is in place, go directly to step 4.
Let's create a file called "update-resolv-conf" in the directory "/ etc / openvpn /"
Code:
$ sudo touch / etc / openvpn / update-resolv-conf
Let's edit it and add the following bash script:
Code:
$ sudo nano / etc / openvpn / update-resolv-conf
After you have pressed Enter, you will see a window for the text editor "nano". Copy the script from here and paste it into the terminal, you can use the right mouse button -> "Paste". In order to save the file, press the hotkey "Ctrl + X", then write the letter "Y" and press Enter. Done, it remains to issue execution rights. We register:
Code:
$ sudo chmod + x / etc / openvpn / update-resolv-conf
We edit the OpenVPN config in any way convenient for you, add 3 lines to the end.
Code:
$ script-security 2
up / etc / openvpn / update-resolv-conf
down / etc / openvpn / update-resolv-conf
We save, reconnect and test (for testing, the site https://dnsleaktest.com/ is suitable.

