sanok
Regular
- Joined
- 28.09.20
- Messages
- 56
- Reaction score
- 160
- Points
- 18
Encryption is the most common and, in fact, the simplest way to protect any information.
However, many might argue, then what is the efficiency and complexity of encryption?
Symmetric ciphers
With them, everything is quite simple.
Asymmetric ciphers
This is a new generation of ciphers that has replaced Symmetric ones.
Programs that provide encryption and hide data under a password
However, some may wonder how encryption can be used. After all, almost everywhere they either impose some method on us, or even do it without our knowledge? Well, okay, we persuaded, you can also tell us about special programs that allow you to encrypt data additionally.
No, don't you dare even think that now we will talk about various small text editors with an encryption function that has been implemented in Word for many years. We will talk about large programs that allow you to hide some folders and files, limiting access to them with a password, or even about giants that encrypt the entire hard drive.
Hide Folder
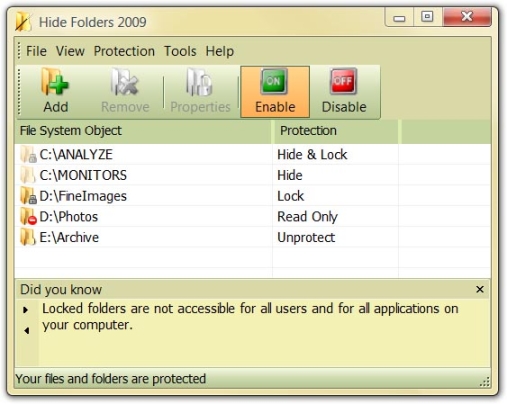
HideFolder User Interface
A simple program with a long history. It allows you to hide folders and files in them from prying eyes. To access the program itself, you need to know the user's password. Implemented simply and with taste, one of the rare cases where brevity is the sister of talent. It doesn't provide data encryption, but it will allow you to hide a collection of obscene photos from your child.As you can see in the image, the program's interface is simple and intuitive.
Files Cipher
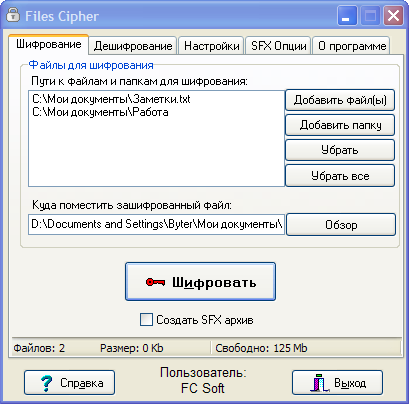
FilesCipher User Interface
A more complex program that already encrypts the file. It was done quite clearly-you selected the file, entered the key to it, and so... and here is the first drawback. The algorithm that the program uses is designed specifically for it, and it is hard to believe that it is really effective. However, the huge key size (from 4 to 255 characters) comes to the rescue. It is also worth noting that this key is not encrypted along with the file, which means that it increases the reliability of the cipher.
TrueCrypt
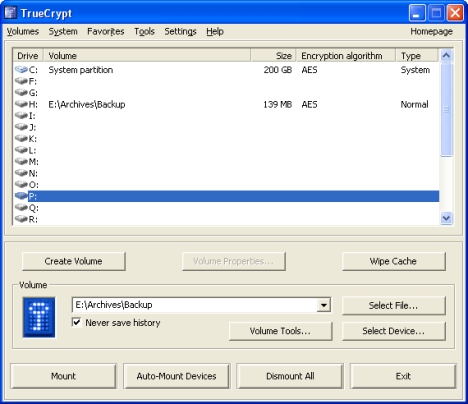
TrueCrypt User Interface
An even more complex program from among the programs for data encryption. Its distinctive feature is not a user-friendly interface and not free, but multi-functionality. Within the framework of this program, the lion's share of existing cryptographic systems (encryption methods) has been implemented.
File Vault
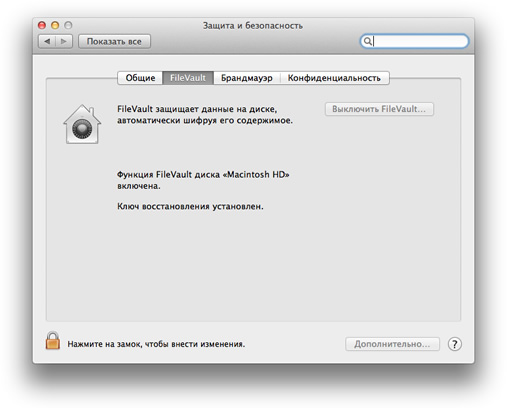
FileVault User Interface
Not so long ago, MAC OS was supplemented with a special FileVault plugin (from English – File Storage), which allows you to encrypt any part of the hard disk, or even the entire disk. This thing works quite simply, it is integrated into the OS kernel and performs encryption/decryption in the background, practically without loading the system and allowing you to calmly go about your business.To encrypt data, you must first enable the plugin, which can be done by going to the menu and selecting the following itemsSystem preferences –> Security). After that, we are asked to enter a master password that allows you to unlock any encryption (useful if, for example, you forgot the password for encrypted information). It is worth noting in advance that if you can't remember the master password and forgot the ciphertext password, then you will have to say goodbye to the data, and it is not possible to restore it in any other way.
The actual encryption and operation algorithm is very efficient and is tied to the current user. By logging in under a different account, even with administrator rights, it is impossible to get through to the necessary files – there will be no access at all. Yes, and it is also impossible to find this disk in any other clever way, so today this is the best way to store personal data on your own PC!
Encryption in VPN connections
It should be mentioned that connecting via a Private Virtual Network (VPN) also provides data encryption. Not all the way along their route, but only between the VPN server and the client, but this is an absolute plus and a powerful tool for data protection. Encryption in a VPN depends entirely on the provider, some provide rather mediocre encryption, some cleverly weave the use of different protocols (for example, VPN and IPsec), which in this case provides a huge level of data protection, and there are some that simply neglect the possibility of encryption in a VPN connection.
Meaning of encryption in general
If you look at it in a comprehensive way, then encryption itself is an excellent tool for protecting information. It can take time equal to days or millennia to select a cipher, key, and crack. But it is important to remember the most important thing that accompanies any cryptographic system (encryption system) – careless handling of keys always leads to hacking. The fewer people who know the password to the data, the less likely it is to crack the ciphertext (the text obtained as a result of encryption).
However, many might argue, then what is the efficiency and complexity of encryption?
Symmetric ciphers
With them, everything is quite simple.
Asymmetric ciphers
This is a new generation of ciphers that has replaced Symmetric ones.
Programs that provide encryption and hide data under a password
However, some may wonder how encryption can be used. After all, almost everywhere they either impose some method on us, or even do it without our knowledge? Well, okay, we persuaded, you can also tell us about special programs that allow you to encrypt data additionally.
No, don't you dare even think that now we will talk about various small text editors with an encryption function that has been implemented in Word for many years. We will talk about large programs that allow you to hide some folders and files, limiting access to them with a password, or even about giants that encrypt the entire hard drive.
Hide Folder

HideFolder User Interface
A simple program with a long history. It allows you to hide folders and files in them from prying eyes. To access the program itself, you need to know the user's password. Implemented simply and with taste, one of the rare cases where brevity is the sister of talent. It doesn't provide data encryption, but it will allow you to hide a collection of obscene photos from your child.As you can see in the image, the program's interface is simple and intuitive.
Files Cipher

FilesCipher User Interface
A more complex program that already encrypts the file. It was done quite clearly-you selected the file, entered the key to it, and so... and here is the first drawback. The algorithm that the program uses is designed specifically for it, and it is hard to believe that it is really effective. However, the huge key size (from 4 to 255 characters) comes to the rescue. It is also worth noting that this key is not encrypted along with the file, which means that it increases the reliability of the cipher.
TrueCrypt

TrueCrypt User Interface
An even more complex program from among the programs for data encryption. Its distinctive feature is not a user-friendly interface and not free, but multi-functionality. Within the framework of this program, the lion's share of existing cryptographic systems (encryption methods) has been implemented.
File Vault

FileVault User Interface
Not so long ago, MAC OS was supplemented with a special FileVault plugin (from English – File Storage), which allows you to encrypt any part of the hard disk, or even the entire disk. This thing works quite simply, it is integrated into the OS kernel and performs encryption/decryption in the background, practically without loading the system and allowing you to calmly go about your business.To encrypt data, you must first enable the plugin, which can be done by going to the menu and selecting the following itemsSystem preferences –> Security). After that, we are asked to enter a master password that allows you to unlock any encryption (useful if, for example, you forgot the password for encrypted information). It is worth noting in advance that if you can't remember the master password and forgot the ciphertext password, then you will have to say goodbye to the data, and it is not possible to restore it in any other way.
The actual encryption and operation algorithm is very efficient and is tied to the current user. By logging in under a different account, even with administrator rights, it is impossible to get through to the necessary files – there will be no access at all. Yes, and it is also impossible to find this disk in any other clever way, so today this is the best way to store personal data on your own PC!
Encryption in VPN connections
It should be mentioned that connecting via a Private Virtual Network (VPN) also provides data encryption. Not all the way along their route, but only between the VPN server and the client, but this is an absolute plus and a powerful tool for data protection. Encryption in a VPN depends entirely on the provider, some provide rather mediocre encryption, some cleverly weave the use of different protocols (for example, VPN and IPsec), which in this case provides a huge level of data protection, and there are some that simply neglect the possibility of encryption in a VPN connection.
Meaning of encryption in general
If you look at it in a comprehensive way, then encryption itself is an excellent tool for protecting information. It can take time equal to days or millennia to select a cipher, key, and crack. But it is important to remember the most important thing that accompanies any cryptographic system (encryption system) – careless handling of keys always leads to hacking. The fewer people who know the password to the data, the less likely it is to crack the ciphertext (the text obtained as a result of encryption).

